Cookie
Index
Purpose
- Assists in maintaining state for web requests (HTTP).
- Local storage in the browser.
Process and Principle
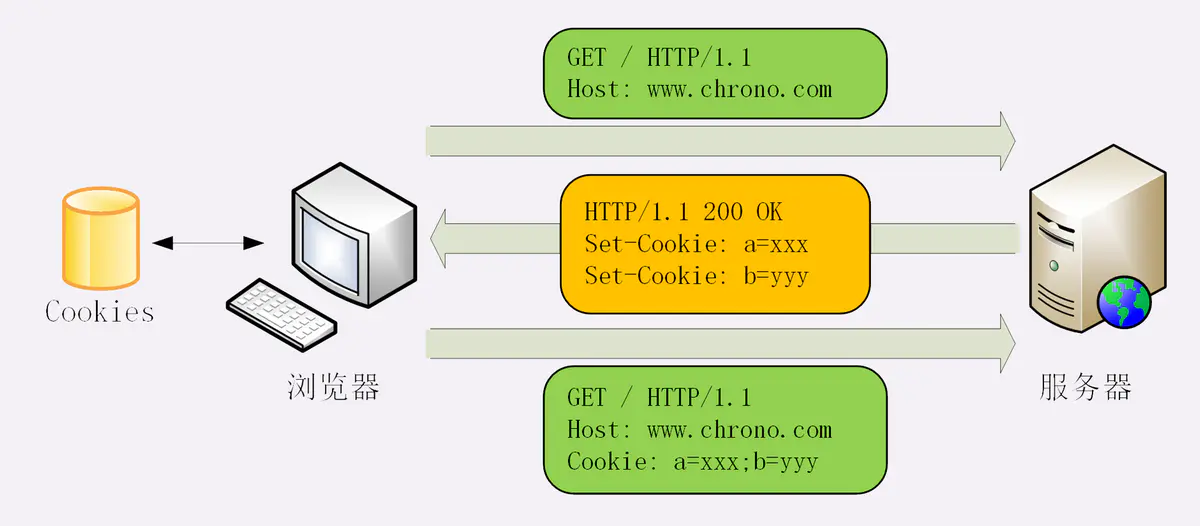
Set Cookie
// response中添加set-cookie头信息
// name=Jerry; expires=Sun, 24-Dec-2023 15:09:07 GMT; Max-Age=60; path=/test; domain=127.0.0.1; secure; httponly
#[GetMapping(path: 'cookie/set')]
public function setCookie(): ResponseInterface
{
$cookie = new Cookie(
name: 'name', // The name of the cookie
value: 'Jerry', // The value of the cookie
expire: time() + 60, // The time the cookie expires
path: '/test', // The path on the server in which the cookie will be available on
domain: '127.0.0.1', // The domain that the cookie is available to
secure: true, // Whether the cookie should only be transmitted over a secure HTTPS connection from the client
httpOnly: true, // Whether the cookie will be made accessible only through the HTTP protocol
raw: false, // Whether the cookie value should be sent with no url encoding
sameSite: null, // Whether the cookie will be available for cross-site requests
);
return $this->response->withCookie($cookie)->json([
'code' => 200,
'msg' => 'ok',
'status' => true,
'data' => [],
]);
}
Use Cases
- Session management (In addition to session management, what other use cases are there for cookies)
- Personalization settings (Frontend configurations that do not require interaction with the backend)
- Browser user behavior tracking.
Considerations
- Cookies depend on the browser mechanism, making them ineffective on mobile devices. Generally, mobile APIs do not rely on cookies for session management. 😅
- If
expireis not set, cookies will be deleted when the browser is closed. - Setting
Access-Control-Allow-Originto*does not work for cross-origin cookie handling. To truly support cross-origin, it should be set to the specific domain. - Cookie values are in plain text, so it is generally recommended to encrypt the values.。
- Each site can store a maximum of
150cookies. - The cookie size limit is 4KB, meaning the
Valuecan be up to 4KB.
Security
CSRF Attack
An attacker can perform sensitive operations using an unexpired cookie. For example:
- Log in to site A (browser sets cookieA), and perform a sensitive operation::
GET https://a.com/transfer/1000; - Click on a phishing link from site B:
<img src="https://a.com/transfer/9999"> - The browser will automatically include cookieA from site A, performing the request, which creates a risk.
【Warning】
Regarding cross-origin cookies: cookies have introduced a sameSite attribute. The values of SameSite are divided into three types: Strict, Lax, and None.
- Strict: Completely prevents third-party cookies. It will not send cookies in any case during cross-site requests.
- Lax: Allows some third-party requests to carry cookies.
- None: Sends cookies regardless of whether it's a cross-site request.
Summary: When SameSite is set to None, Secure must be true, meaning you must use HTTPS for the request. With this configuration, you can carry cookies in cross-origin requests.
